FIDO2 Review

2 Factor, a nightmare#
So you want to add 2 factor to your accounts, because passwords alone are limited by our meaty brains to remember them, and can be stolen/cracked. You’ve got some options:
SMS#
Send a one-time password (OTP) to your phone via SMS. This doesn’t work great, since I don’t always have my phone. It gets lost, it gets broken, it gets stolen. I don’t always have the same SIM when travelling. Not to mention the code can be intercepted by
- Malware on your phone
- Fraudsters SIM swapping, (slowly getting less of an issue.)
- Phishing websites
- Your phone company, ∴ Governments.
Auth App#
Have an app on your phone generate Time-based one-time passwords (TOTP). Same issues for broken and lost phones. Often each will demand their own app even though there is an established standard for otpath URIs. Are a bit more secure than SMS at least.
I hate my phone#
Along with the practical problems, and the privacy problems of handing your phone number to every service, I also just hate the idea of having my digital life locked to my phone for some reason.
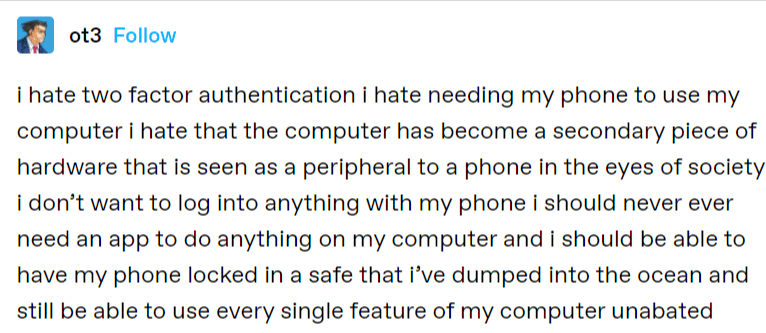
Couldn’t have said it better myself. Well, I would have used sentences.
Email OTP#
Finally we are getting somewhere on the usability scale. Like SMS, Email isn’t E2E encrypted but the world has decided it’s good enough. I can read my email on any device anywhere in the world. But how does one 2 factor their email? Another email account? I guess two passwords are better than one but not a lot better. Still vulnerable to phishing too.
Hardware key#
Fuck yeah now I feel like a spy. These have always seemed exotic and weird to me. Only limited services work with them, they use mystery proprietary techniques to function. Often they’d be some type of TOTP and pretend to be a USB keyboard and just type the code in.
Things are getting better. U2F came along and was kind of popular with Googlers. Now FIDO2 (WebAuthn + CTAP2) is actually picking up steam in the last few years. U2F was renamed CTAP1, while FIDO1 doesn’t exist. They are sometimes also called passkeys, because the naming wasn’t confusing enough yet. At least, we have one key and protocols that covers everything between your web browser and USB port. It works on Apple, Microsoft, and open source software.
Instead of a single secret, these work with asymmetric key cryptography, similar to SSH or TLS. So when you authenticate, your private key never leaves the yubico hardware. Apart from the cozy feeling of actually holding your key in your hand, this gives some bonus benefits.
Actual phishing protection. 2 factor authentication is often claimed to combat phishing attacks, but it doesn’t help all that much. Nothings stopping you from entering both password and 2nd factor code into the same malicious site. FIDO2 includes the domain of the site you’re logging into to make sure only the same website authenticates with its own key. Sort of similar to how SSH will refuse to authenticate if the server’s details don’t match previous logins. I put this claim to the test myself on this blog.
A private key that doesn’t leave your device. During logins the website will send your key some nonce data to sign with it’s private key. It can then check with their copy of your public key. Even if a website’s account data is breached, no amount of offline cracking will give them a hint of what your private key is. Also every website you register on gets a unique keypair.
You can read the FIDO Security Reference/Review to see the risks and mitigations they’ve thought through. Of course there’s problems like ‘your key is stolen’ or ‘it was manufactured with a backdoor’. But that’s why you keep using a password as well.
Introducing the Yubico Security Key#
So I bought this guy, with a very confusing name, since everything Yubico make can be called a security key. It’s basically the same hardware as the Yubico 5 but with all of the bells and whistles removed, it only does U2F and FIDO2, though for half the price!
It works really well! Windows, Linux, Mac, Android, Firefox, Chrome, and Safari could use it no problems, no drivers, no setup required. You plug it in, then tap the capacitive logo to say “Yes I am a real human using this key in real life”.
The problems only start with each of the services. Since FIDO2 only really specifies communicating with a authentication server, exactly how it works is up to the developer. To enroll the key for my Apple account, I was forced to use my Mac’s System Settings app, for no real reason. When attempting to enroll the key for my Microsoft account, it would do so not as a 2nd factor, but as a replacement for my password. This is obviously worse, so they also make you set a PIN (password) for the hardware key. This PIN is set on the key, and would need to be entered for every other account in the future, something I don’t really want when already using unique passwords for each. It would add a third step to every other account login process.
Another issue with this wild west software situation is how unclear the status of the hardware key is. The key can only fit 25 accounts, but there’s no way to list out what accounts are already registered and how close to the limit you are. There’s no UI to see the status or configuration of the hardware key. This is partly by design, as the idea is for one service never to see other accounts on the key and leak identifying details.
While the major tech companies support FIDO2, many webapps and services don’t and probably won’t for a long while. Given the limited number of accounts a key can fit, I’d suggest setting it up for your email and password manager accounts only. That way you can keep all your eggs in one basket, but at least make it a really secure basket.
Recovery#
Each service has their own account recovery mechanisms. Just in case I loose or break my hardware key, I bought two and could enroll both to all of my accounts. Most services will have an escape hatch, from recovery keys you’re meant to write down, email/phone codes, or calling customer support for hours. I don’t want to be stuck relying on these methods so two keys covers me.
Chinks in the armour#
So the classic problem with 2 factor auth is that it doesn’t exist everywhere. FIDO2 does a great job when logging into a website, but sometimes I still prefer native apps. My email is accessed by IMAP, which doesn’t support any 2 factor. So anyone with just my IMAP password can get complete access to my emails.
Bitwarden’s Mac app also doesn’t currently work with FIDO2, so it falls back to email. Combine that with the IMAP problem and you have a path to takeover all of my accounts without needing my security key at all.
It doesn’t make the hardware key totally useless, but it’s important to keep in mind. I’m still left with an account that’s harder to access, since my separate IMAP password can be way longer than my brain can remember.
The Fall#
Unfortunately FIDO2 is annoying to practically use since it lacks focus, trying to be too much at once. It’s not just for security keys, device TPM’s can do the same (We’re back to the Mobile App problems 😰). Then they thought, “heck why even do 2 factor auth? Let’s make FIDO2 the one and only factor! Passwordless baby! Passkeys!”
Except that actually is less secure, anyone with the key can get into your account, we’re down to a single factor again. Let’s chuck a password on the key when used. Let’s call it a PIN instead so we can keep saying the buzz word passwordless.
Every OS/browser/tech fiefdom have realised that phone screens break and that users can’t be trusted to hold the keys to their accounts, so they’ve made their own cloud keypass management systems that are exactly like password managers but somehow more fiddly, and locked to their ecosystem. Make an account on your Mac and want to login via your PC? Too bad, that passkey is locked in your iCloud account and you will only ever be able to use it on an Apple device. The FIDO alliance never made a protocol to sync or export passkeys between devices and don’t seem to give a shit about making one. They seem happy with this vendor lock-in situation.
HOW DOES A PASSKEY BECOME AVAILABLE ACROSS A USER’S DEVICES?
When a user creates a passkey on any of their devices, it gets synced to all the user’s other devices running the same OS platform which are also signed into the same user’s platform account. Thus passkeys created on one device become available on all devices.
- FIDO Alliance FAQs
So when you go to use a FIDO2 service, you’re greeted with a clusterfuck of competing options. Every OS/browser/tech fithdom will offer to be the shittiest password manager for you. Bitwarden will jump in and say “Hey this website wants to set up a key, I’ll pretend to be one for you.”.
Then Windows will pop up. “Hey yo this site is looking for a security key, but instead you should just let me save it to your PC yeah? Or how about you download the Microsoft authenticator app on your phone and connect to your PC over bluetooth, that’s an option I’m going to suggest as a default. Everytime. Even if you never set it up. Or have bluetooth.”
I tried setting up some virtual keys/passkeys with Bitwarden, thinking a wholesome, smol, nordic, third party password manager would be the best bet to sync and use my keys on all platforms. Unfortunately I learnt the hard way that actually you can’t use these on mobile. Turns out this is mostly an issue with Bitwarden’s app, and not a limitation imposed by Android. Hopefully it’s fixed soon. Also Bitwarden won’t let you export or transfer passkeys it stores, with them simply omitted from vault exports.
All this to say, software based keys using the FIDO2 system are still a bit of a mess, even after years of development. It might get better, but don’t hold your breath since the major players are very happy with the current situation. The saving grace is that you can have multiple passkeys enrolled to one account. Normal users are going to end up with a trail of lost and broken keys on each account and still just use a normal password to login on new devices, giving their accounts no extra security. Oh Well.
Comment
- Username, 2026-01-27